TL;DR - Even with MFA enabled on firefly III versions v6.1.16 and lower, an attacker is able to authorize OAuth applications against user accounts using only a username and password.
Advisory can be found here.
Firefly III is a personal finance manager which is both free and open source for anyone to use. After a recommendation from a colleague, I decided to spin up a version for myself.
I configured my Firefly account with a strong password + MFA. The login flow with such looks like the following:

Followed by an enforced MFA prompt:
After which, I simply started playing with the application and exploring it from the view set of personal usage. As a part of this, I explored the applications ability to automate data importation. After all, I don’t want to manually add every transaction I make!
Of course, this is a solved problem and comes pre-packed with the application… Insert the aptly named data import tool.
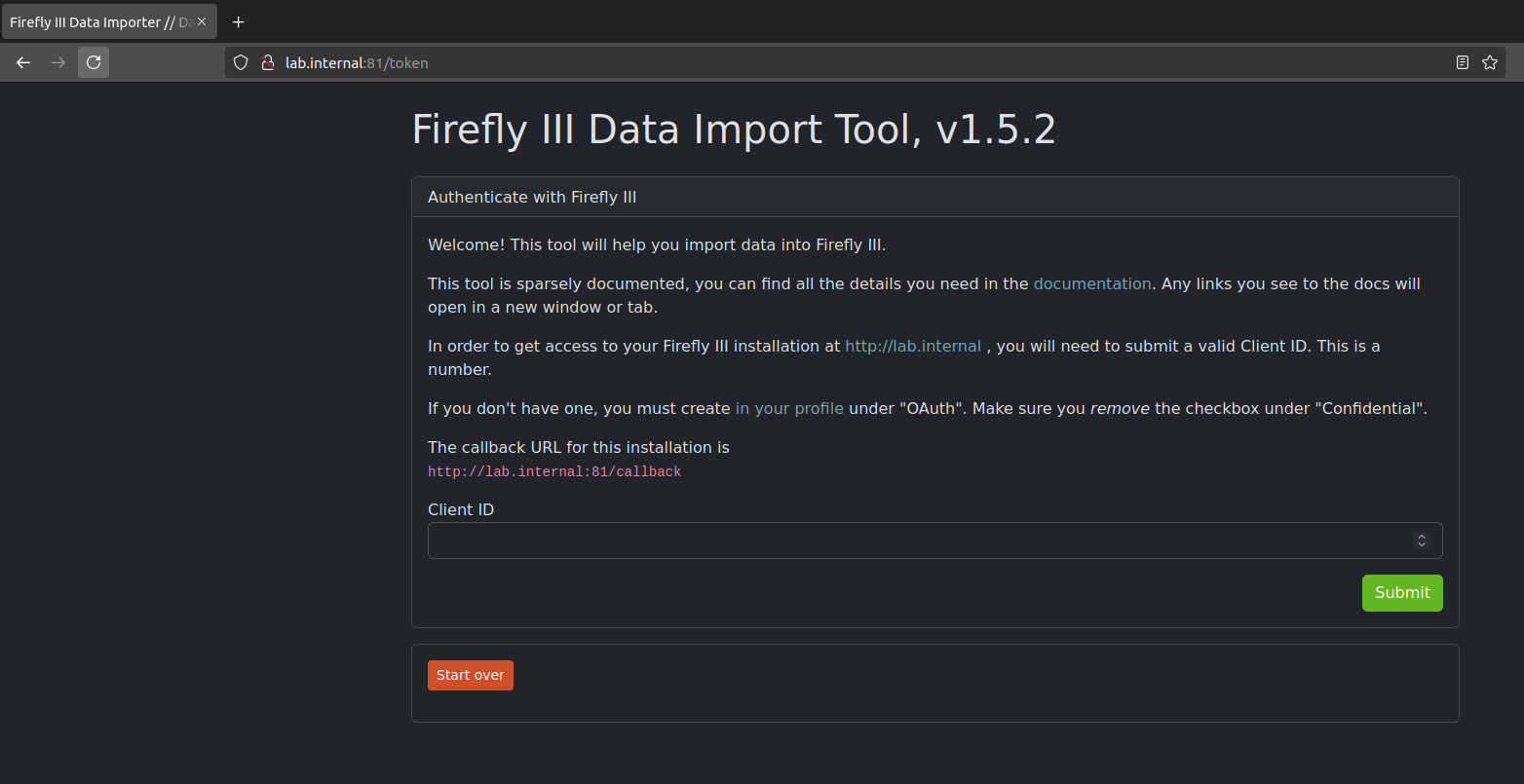
I did notice during the creation process for this, that the client ID is a sequential number. This would allow us to easily just attempt to brute force an application if we wanted to do something like phishing, or test to see if a Firefly user has any OAuth clients configured (Further reading material can be found here).
Alas that’s not the primary issue here.
So what happens if we attempt to set this tool up? Let’s put in a valid client ID and click “Submit”. Well, we get a login prompt (I’d logged out of the primary application) as expected.

However, when we click “Sign in” we are prompted with the following:
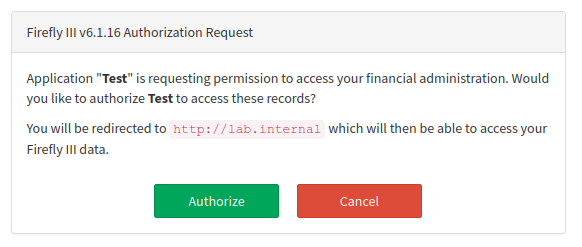
That’s not MFA? And if we click authorize what happens?
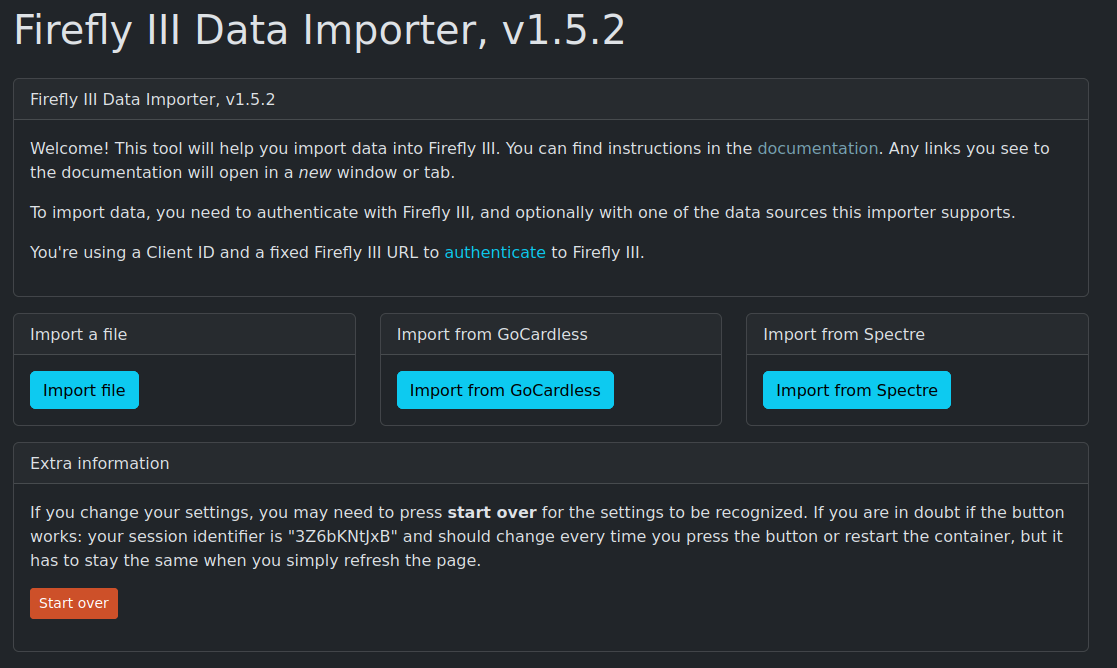
Well it looks like it’s good to go. That ain’t ideal!
Anyway that’s it. Not very technical this time around, but still quite a risky issue given the kinds of access the API has to user data. Happy hacking and I’ll cya again next time.
A thought on firefly’s security processes Link to heading
In a word? Amazing.
The response to this disclosure and subsequent discussions have honestly been great. It’s funny to think that out of my experiences, it’s often the open source communities who impress me most. Interactions with James (JC5) have been very pleasant and the overall vibe is just a couple of people working towards a common goal of securing software.
It may also be slightly biased; and/or lucky; but he did also respond to my initial disclosure in 17 minutes.